Disaster Recovery and business continuity
When we talk about software security and business continuity of a business we have to think about two main plans. The first one is we should have a Business Continuity plan (BCP). That means the activities which are needed to keep the organization running or working during a period of time that is the interruption or displacement of our normal operations. Another thing is we need to have a Disaster Recovery Plan (DRP). Which means the process of rebuilding the operations or infrastructure of the company after the disaster has passed.
For your knowledge BCP and DRP are two different things. BCP stands for keep the organization running during a period of time which the interruption or displacement happens. But the DRP means that process of rebuilding the operations or infrastructure of the company after the disaster has passed.
Business Continuity Plan – BCP
The business continuity plan is focused on the ‘Availability’ of the CIA. This helps the continuation of the critical business processes when the disaster destroys the data processing capabilities. This focus is on getting the critical systems to another place while repairing of original facilities and the right people to the right places. This allows organizations to perform business in different modes until regular conditions of the original place are back to normal.
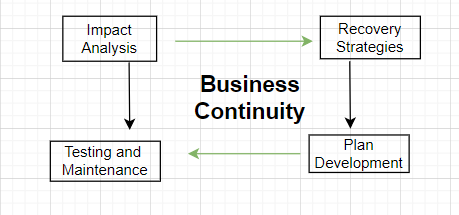
Preparation, Testing, and Maintenance help to recover normal processing.
Methods Achieve Business Continuity
- Cold Site
- Hot Site
- Mirrored Site
Cold Site
An empty facility located away from the particular site with the required infrastructure.
Hot Site
A site with hardware, software, and network installed and compatible with the original site.
Mirrored Site
A site that has all the facilities similar to the original system with Mirroring capability. In the mirrored sites data is mirrored and backed up.
BCP ensures redundancy and minimizes the cost.
Disaster Recovery Planning – DRP
Same to BRP this also focuses on the ‘Availability’ of the CIA triad. This helps to minimize the effect of the disaster by taking steps and actions by ensuring to resume the people, resources, and business processes in a normal manner with time.
DRP Key Activities
- Identify critical systems
- Data backups and restoration.
Disaster recovery goals
- Reduction of the risk that may happen to the business
- Address investors
- Resume operations
Benefits of BCP and DRP
- Reduced risk
- Process improvements
- Marketplace advantage
Software Security
Software security is a concept of effecting or implementing mechanisms during developing software to help it remain functional to attacks.
Types of Software Security
- Cloud Security
- Network Security
- Endpoint security
Software Vs. Application Security
Application Security
Application security is used to defend the software exploit after the deployment is complete.
Examples:-
- Threat modeling
- Code review
- Penetrate
Software Security
Software security is a way to defend the software exploit by building software to be secure.
- Root cause analysis
- organizational change
Attacks on Software
Types of Attacks
- Leakage
- Tampering
- Resource Stealing
- Vandalism
- Denial of service
Here leakage means the information which we have leaving from the system, Tampering means information changing without access, and Resource stealing means the illegal use of resources. Vandalism means the distribution of the correct system operations which means some users can use the services to be effective for the normal operations of the system. A little bit the same as that Denial of service also means that it disrupts the legitimate use of the system. As an example, if the users can use the system more and the availability of the system goes down.
Methods of attack
- Eavesdropping – Obtaining the message copies without authority
- Masquerading – Using the identity of another principal without authority
- Message tampering – Altering messages
- Replaying – Storing messages and sending them later
- Flooding – Sending too many messages
Issues with Security breaches
- Immediate Financial lost
- Lawsuits
- Reputation
Secure Software Development Lifecycle
Secure Software Development Lifecycle (S-SDLC) means that applying the security steps in every step of software development.
Now Let’s see how the SSDLC affects every phase of the below sample lifecycle.
- Requirement Gathering –
- Risk Assessment
- Design
- Threat Modeling
- Coding
- Code Review
- Testing
- Vulnerability Assessment
- Deployment
- Network Configuration Review
- Server Configuration Review
Aspects of Software Security
* Cryptography
* Penetration Testing
* Vulnerability Assessment
* Code level security, User Input Verification